On Tuesday, an attacker drained more than $10 million from a smart contract belonging to LI.FI, a DeFi protocol known for its services as a bridge and decentralized exchange aggregator. The wallet address that exploited the smart contract has since transferred out almost all of the drained funds.
“A smart contract exploit earlier today has been contained and the affected smart contract facet disabled,” LI.FI wrote on X at 11:44 a.m ET. “There is currently no further risk to users. The only wallets affected were set to infinite approvals, and represented only a very small number of users.”
A smart contract exploit earlier today has been contained and the affected smart contract facet disabled.
There is currently no further risk to users.
The only wallets affected were set to infinite approvals, and represented only a very small number of users.
We are engaging…
— LI.FI (@lifiprotocol) July 16, 2024
According to blockchain analytics firm Nansen, the wallet address that exploited LI.FI was initially funded by Tornado Cash. Two of Tornado Cash’s primary developers – Roman Storm and Roman Semenov – are facing federal prosecution by the US Department of Justice for money laundering. Meanwhile, a Dutch court rejected bail this week for Tornado Cash’s other developer, Alexey Pertsev, as reported by DLNews.
After the wallet address (0xd82) exploited a smart contract and received the funds drained from LI.FI, the exploiter proceeded to, among other actions, interact with decentralized exchange Symbiosis, transact on Uniswap, and transfer millions of dollars worth of ETH out to different addresses, onchain data shows.
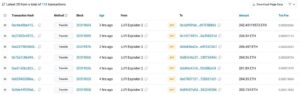
These seven transfers represent some of the money that was drained from LI-FI. (Etherscan)
How It Happened
According to Ido Ben-Natan, the CEO of crypto security tools provider Blockaid, the attackers deceived LI.FI’s proxy contract – a router that mediates between users and the protocol – into initiating unauthorized transfer commands to the protocol.
“The attackers have managed to exploit a vulnerability in the proxy implementation. An attacker is able to inject function calls to the contract, which they’ve then used to inject transfers from calls on approved users,” Ben-Natan told Unchained over email. “What happened was that a proxy contract, which was used as a trusted approval spender for swapping purposes, got exploited into transferring approved assets to a malicious destination.”
On X, the LI.FI team added that they are also working with law enforcement and third parties to follow the trail of funds that left the protocol.
Not LI.FI’s First Exploit
LI.FI has been the victim of unauthorized transfers before.
According to security firm Peck Shield, the Tuesday’s exploit impacting LI.FI arose from basically the same bug that had affected the same protocol two years ago,
“While analyzing today’s @lifiprotocol hack, we notice[ed] an earlier hack on the same protocol on March 20, 2022, wrote Peck Shield on X. “The bug is basically the same.”
@Zord4n, who handles marketing for LI.FI according to their X profile, wrote on the day of the March 2022 hack about how a vulnerability caused 29 wallets to lose a combined total of roughly $600,000.
“As a result of the exploit, anyone who gave infinite approval to our contract was vulnerable,” @Zord4n wrote in 2022.
On Tuesday, LI.FI team used similar language in their post on X about how only wallets with infinite approval settings were impacted.
“We’re working on a post mortem that’ll get you all the information,” LI.FI founder and CEO Philipp Zentner told Unchained.



